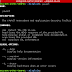
DracOS - Lightweight and Powerful Penetration Testing OS
 Reviewed by Zion3R
on
11:30 AM
Rating:
Reviewed by Zion3R
on
11:30 AM
Rating:
 Reviewed by Zion3R
on
11:30 AM
Rating:
Reviewed by Zion3R
on
11:30 AM
Rating:
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:12 AM
Rating: 5
Reviewed by Zion3R
on
11:12 AM
Rating: 5
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:00 AM
Rating: 5
Reviewed by Zion3R
on
11:00 AM
Rating: 5
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:12 AM
Rating: 5
Reviewed by Zion3R
on
11:12 AM
Rating: 5
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:12 AM
Rating: 5
Reviewed by Zion3R
on
11:12 AM
Rating: 5
 Reviewed by Zion3R
on
11:46 AM
Rating: 5
Reviewed by Zion3R
on
11:46 AM
Rating: 5
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:26 AM
Rating: 5
Reviewed by Zion3R
on
11:26 AM
Rating: 5
 Reviewed by Zion3R
on
5:47 PM
Rating: 5
Reviewed by Zion3R
on
5:47 PM
Rating: 5
 Reviewed by Zion3R
on
11:36 AM
Rating: 5
Reviewed by Zion3R
on
11:36 AM
Rating: 5
 Reviewed by Zion3R
on
11:11 AM
Rating: 5
Reviewed by Zion3R
on
11:11 AM
Rating: 5
 Reviewed by Zion3R
on
10:52 AM
Rating: 5
Reviewed by Zion3R
on
10:52 AM
Rating: 5
 Reviewed by Zion3R
on
6:42 PM
Rating: 5
Reviewed by Zion3R
on
6:42 PM
Rating: 5
 Reviewed by Zion3R
on
1:02 PM
Rating: 5
Reviewed by Zion3R
on
1:02 PM
Rating: 5
 Reviewed by Zion3R
on
1:37 PM
Rating: 5
Reviewed by Zion3R
on
1:37 PM
Rating: 5
 Reviewed by Zion3R
on
11:12 AM
Rating: 5
Reviewed by Zion3R
on
11:12 AM
Rating: 5
 Reviewed by Zion3R
on
11:30 AM
Rating: 5
Reviewed by Zion3R
on
11:30 AM
Rating: 5
Copyright © KitPloit - PenTest & Hacking Tools
Back To Top