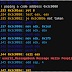
wmiexec-RegOut - Modify Version Of Impacket Wmiexec.Py, Get Output(Data,Response) From Registry, Don'T Need SMB Connection, Also Bypassing Antivirus-Software In Lateral Movement Like WMIHACKER
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
Bluffy - Convert Shellcode Into Different Formats!
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
Whatfiles - Log What Files Are Accessed By Any Linux Process
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
Advertisement
Scemu - X86 32bits Emulator, For Securely Emulating Shellcodes
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
Shellcode-Encryptor - A Simple Shell Code Encryptor/Decryptor/Executor To Bypass Anti Virus
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
RPC Firewall - Stopping Lateral Movement via the RPC Firewall
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
Advertisement
Lsarelayx - NTLM Relaying For Windows Made Easy
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
PMAT-labs - Labs For Practical Malware Analysis And Triage
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
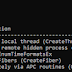
Jektor - A Windows User-Mode Shellcode Execution Tool That Demonstrates Various Techniques That Malware Uses
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
DLLHijackingScanner - This Is A PoC For Bypassing UAC Using DLL Hijacking And Abusing The "Trusted Directories" Verification
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
XC - A Small Reverse Shell For Linux And Windows
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
ZipExec - A Unique Technique To Execute Binaries From A Password Protected Zip
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
Digital-Forensics-Lab - Free Hands-On Digital Forensics Labs For Students And Faculty
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
OffensiveRust - Rust Weaponization For Red Team Engagements
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
DetectionLabELK - A Fork From DetectionLab With ELK Stack Instead Of Splunk
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
Nanobrok - Web Service For Control And Protect Your Android Device Remotely
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
LOLBins - PyQT5 App For LOLBAS And GTFOBins
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
SillyRAT - A Cross Platform Multifunctional (Windows/Linux/Mac) RAT
Reviewed by
Zion3R
on
8:30 AM
Rating:
5
Registry-Recon - Cobalt Strike Aggressor Script That Performs System/AV/EDR Recon
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
EXOCET - AV-evading, Undetectable, Payload Delivery Tool
Reviewed by
Zion3R
on
5:30 PM
Rating:
5
 Reviewed by Zion3R
on
5:30 PM
Rating:
Reviewed by Zion3R
on
5:30 PM
Rating:
 Reviewed by Zion3R
on
5:30 PM
Rating:
Reviewed by Zion3R
on
5:30 PM
Rating: