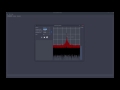
Universal Radio Hacker - Investigate Wireless Protocols Like A Boss
 Reviewed by Zion3R
on
10:11 AM
Rating:
Reviewed by Zion3R
on
10:11 AM
Rating:
 Reviewed by Zion3R
on
10:11 AM
Rating:
Reviewed by Zion3R
on
10:11 AM
Rating:
 Reviewed by Zion3R
on
10:11 AM
Rating: 5
Reviewed by Zion3R
on
10:11 AM
Rating: 5
 Reviewed by Zion3R
on
6:47 PM
Rating: 5
Reviewed by Zion3R
on
6:47 PM
Rating: 5
 Reviewed by Zion3R
on
11:09 AM
Rating: 5
Reviewed by Zion3R
on
11:09 AM
Rating: 5
 Reviewed by Zion3R
on
6:15 PM
Rating: 5
Reviewed by Zion3R
on
6:15 PM
Rating: 5
 Reviewed by Zion3R
on
10:32 AM
Rating: 5
Reviewed by Zion3R
on
10:32 AM
Rating: 5
 Reviewed by Zion3R
on
5:34 PM
Rating: 5
Reviewed by Zion3R
on
5:34 PM
Rating: 5
 Reviewed by Zion3R
on
5:37 PM
Rating: 5
Reviewed by Zion3R
on
5:37 PM
Rating: 5
 Reviewed by Zion3R
on
10:45 AM
Rating: 5
Reviewed by Zion3R
on
10:45 AM
Rating: 5
 Reviewed by Zion3R
on
7:30 PM
Rating: 5
Reviewed by Zion3R
on
7:30 PM
Rating: 5
 Reviewed by Zion3R
on
10:29 AM
Rating: 5
Reviewed by Zion3R
on
10:29 AM
Rating: 5
 Reviewed by Zion3R
on
7:31 PM
Rating: 5
Reviewed by Zion3R
on
7:31 PM
Rating: 5
 Reviewed by Zion3R
on
11:01 AM
Rating: 5
Reviewed by Zion3R
on
11:01 AM
Rating: 5
 Reviewed by Zion3R
on
7:46 PM
Rating: 5
Reviewed by Zion3R
on
7:46 PM
Rating: 5
 Reviewed by Zion3R
on
6:35 PM
Rating: 5
Reviewed by Zion3R
on
6:35 PM
Rating: 5
 Reviewed by Zion3R
on
10:30 AM
Rating: 5
Reviewed by Zion3R
on
10:30 AM
Rating: 5
 Reviewed by Zion3R
on
10:30 AM
Rating: 5
Reviewed by Zion3R
on
10:30 AM
Rating: 5
 Reviewed by Zion3R
on
11:09 AM
Rating: 5
Reviewed by Zion3R
on
11:09 AM
Rating: 5
 Reviewed by Zion3R
on
10:12 AM
Rating: 5
Reviewed by Zion3R
on
10:12 AM
Rating: 5
 Reviewed by Zion3R
on
11:09 AM
Rating: 5
Reviewed by Zion3R
on
11:09 AM
Rating: 5
 Reviewed by Zion3R
on
11:12 AM
Rating: 5
Reviewed by Zion3R
on
11:12 AM
Rating: 5
Copyright © KitPloit - PenTest & Hacking Tools
Back To Top